Quick answer: It’s clear that ZTNA is a better and more secure solution for enterprises. While a VPN will blindly trust any authorized device, ZTNA will scan and analyze various factors of each device, giving very limited access to the company’s assets due to its zero-trust approach.
Since the COVID outbreak in 2019, many people were forced to work from home. This trend further made enterprise security a lot more important, given the remote information sharing that happens in the process. Making sure that the connection is safe and secure, a VPN seemed like a viable option for a long time.
However, with the rising popularity of ZTNA, VPNs started showing their limitations. Although, for more than a decade, a Virtual Private Network was a go-to option for safeguarding enterprise networks. Regardless of what we said, using a VPN for this purpose isn’t as popular as it was before
But, you should keep in mind that both solutions have their advantages and disadvantages, which depend on your needs. Thus, in today’s article, I will give you a comprehensive ZTNA vs VPN comparison and see which solution is actually better.
1. What Is a VPN?
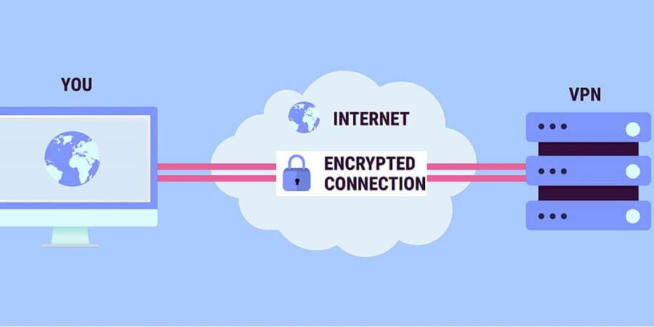
Let’s start this article by talking about a VPN. A VPN stands for Virtual Private Network and it’s here to encrypt your connection, which makes it untraceable by a third-party entity. While it’s very often used by individuals, there are so-called business VPNs that companies can purchase.
In this case, the sole purpose is the privacy and security of the company. By connecting to a VPN, users will secure their connections and be able to transfer information and files from their homes to the company securely. So, how does a VPN work actually?
Well, to use a VPN, you need to have an application through which you’ll connect to the VPN server. Before that, the company needs to purchase a VPN subscription, where each user will get his login credentials – password and username.
Once that is in place, users can simply log in, connect to the server, encrypt their connection, and enjoy all the benefits. For non-business users, a VPN is the ultimate tool for online privacy and security. However, in terms of using it for businesses, VPNs do have a few limits compared to ZTNA.
We’ll address them once we explain what is ZTNA.
2. What Is ZTNA?
To clarify what is ZTNA, we first need to see what this abbreviation means. ZTNA stands for Zero-Trust Network Architecture and unlike VPN, it trusts no one. What does this mean? Well, while using a VPN, users can transfer all types of files securely and access the company’s resources effortlessly.
In ZTNA, that is not entirely possible because this solution restricts access to resources, so users require an allowance to access some of them. The good (or bad) thing is that this applies even if a user already accessed a particular part of the company’s resources.
If he tries to do it again, he’ll still get a restriction until the network administrator allows it. In many cases, a user will need to go through a complex verification process, despite being a long-time employee. As you can see, the zero-trust model is quite strict when it comes to security.
While this ensures that your data will most likely never get compromised, there’s one downside of this solution. Namely, users must remember their credentials and they must be updated frequently to make ZTNA efficient.
If a user can’t complete the authentication process, he or she will not be able to access the required resources. And, due to its zero-trust approach, ZTNA will not allow a user to access them without going through this process.
3. Which ZTNA Software Do We Recommend?
If you made up your mind and you need ZTNA, we’ll briefly talk about our favorite choice – Perimeter 81 Zero Trust Platform. ZTNA claims to severely overpower legacy VPNs with rock-solid security and tons of useful features.
It offers the least privilege access, preventing unauthorized devices and users from accessing your data. As such, the risk of cyberattacks is brought to zero. Moreover, Perimeter 81 monitors your network 24/7, keeping impostors away from your valuable files.
To make sure your network is fully secured, Perimeter 81 takes advantage of encryption. With 256-bit AES encryption and WireGuard, OpenVPN, and IPsec protocols, keeping untrustworthy devices away is a breeze.
The best thing is that Perimeter 81 Zero Trust Platform is very easy to set up. In a few minutes, you can segment the entire network, give out permissions, and start enjoying 100% secure access. Perimeter 81 starts at $8 a month per gateway with a minimum of 5 users.
Not to mention a 30-day unconditional money-back guarantee, letting you test out Perimeter 81 without the risk of losing any money. All in all, if you need more security and better performance than a VPN, Perimeter 81 is your best bet.
4. Limits of a VPN
In this ZTNA vs VPN comparison, it’s pretty clear that a VPN has much more disadvantages compared to ZTNA. Once again, a VPN is a great solution if browsing the web anonymously is your goal.
But, in the corporate world, VPNs have a few flaws that make them less secure than ZTNA solutions.
4.1 Perimeter-Based Security Approach
Perhaps the biggest drawback of a VPN is its perimeter-based security approach. What exactly does it mean? Well, let’s take your company’s network as an example. Users who connect to a VPN can access this network fully and use the company’s resources as they wish, with no identity checks or verifications.
With no other security implementations in place, your network is always exposed to threats of all sorts. I mean, just think about it – is it good to trust every user in the network to have full access to the company’s files and information just like that?
By doing so, you potentially put your company at risk by exposing crucial information to each user. Basically, once a user connects to a VPN, it has no clue as to which files and information he or she transfers and uses.
This is especially dangerous if you have employees working from home. They will most likely save the company’s files to their computers, which are, oftentimes, full of malware due to other internet activities that users perform.
Through malware, hackers can easily hijack their computers and access those files, compromising your company’s integrity. On the flip side, VPNs are more secure for users connecting from a corporate environment with other security measures in place.
However, even in that case, its perimeter-based approach isn’t great for completely securing your company’s resources. Not to mention that many VPNs have had multiple security breaches and exploits, with many users’ accounts stolen.
4.2 Not the Best Performance
Now, what about performance? Well, popular VPNs like ExpressVPN and NordVPN are known for delivering great speeds for individual users. When it comes to corporate needs, a VPN simply isn’t fast enough to satisfy an intense working environment.
You should know that VPNs route your traffic through a remote VPN server located somewhere else. Thus, the speed of your connection will greatly depend on the distance between you and that server. With encryption in place, the connection is more secure but also slower.
If you have a hard day at work, with lots of tasks, this lack of performance can produce a delay. In this case, uploading and downloading files will be slower, and if you attend webinars or video conferences, you’ll most likely experience lags and slowdowns.
4.3 Software Vulnerabilities
As said, VPNs depend on their software as it allows users to connect to a VPN server. To implement a VPN, the company’s employees must install a VPN app to be able to use it. However, these applications aren’t perfect and some of them are known to have vulnerabilities that hackers exposed over time.
Also, beware that VPN providers publish their updates and patches from time to time. Therefore, users need to be careful and install them accordingly because they usually improve security. Cybercriminals and hackers often scan the network for non-updated software that they can exploit.
And if they manage to track the user that hasn’t updated his VPN app, they can easily perform a security breach and hijack the account. With access to your employee’s VPN account, hackers can get a hold of your company’s information and jeopardize it.
4.4 Lack of Cloud Support
Last but not least, VPNs lack cloud support. Remember – their security is perimeter-based and some companies store important information on a cloud. Since a VPN cannot protect cloud storage, this means that your cloud-based information gets no protection.
5. So, Is ZTNA Any Better?
Given VPN’s limitations, the question is – is ZTNA better in this ZTNA vs VPN comparison? Well, to be honest, for the majority of modern businesses, ZTNA will do much more in terms of security and overall performance.
Here’s why:
5.1 Zero-Trust Approach
We said that ZTNA takes a so-called zero-trust approach to security. Rather than going with the open network philosophy of VPNs, ZTNA solutions give very limited access to the company’s resources and require special clearances for users to access them.
You see, a VPN deems anyone trustworthy once the device or user passes the network perimeter. If you have a VPN and connect to a VPN server, you’re free to do whatever you want. On the other hand, ZTNA is quite the opposite – it sees every device or user as untrustworthy.
For example, you can have access to one area of the network, but if you try to go anywhere else, ZTNA will forbid access. Also, even if you’ve accessed that part of the network before, ZTNA will request from you to go through a verification process to access it again, making security the utmost priority.
We can take hackers and cybercriminals as an example here. They can try to access the network externally, but ZTNA will spring into action, see them as untrustworthy, and block their access. Simply put, it forbids access to EVERYONE unless it’s proven that they can be trusted.
Compared to the VPN, if a user account gets compromised, a cybercriminal will have the required username and password. Given its open network approach, a VPN will, in this case, allow him to access all applications and files with no required clearance or verification.
5.2 Great Performance
Unlike VPNs, ZTNA offers much better performance and speed. VPNs take some time to set up, especially since you need to install the app, choose the server, and wait for the virtual tunnel to be placed.
ZTNA solutions are usually cloud-based and they focus on secure access to apps and the company’s resources. They don’t require you to connect to a remote server, and as such, they have pretty much no impact on the performance.
Moreover, ZTNA works in the background and does everything else for you. Once you click on the app you want, ZTNA authenticates and verifies your device, making sure your firmware is up to date, which is necessary for secure access.
This all happens in a split second, so you don’t even notice it. Not to mention that accessing apps and resources is much easier because it doesn’t depend on which network you are. Once ZTNA verifies your identity, you can use your device to access applications no matter where you are located.
5.3 Complex Infrastructure
Having a complex infrastructure is crucial for providing complex security solutions. Unlike VPNs that aren’t scalable and can’t protect multiple endpoints, ZTNA solutions offer all-around protection. A testament to that is its support for cloud-based workplaces.
This means that it applies the same rules for apps and files located on a cloud, where it employs its zero-trust security approach. Even if a cybercriminal locates your public or virtual cloud space, accessing it will be impossible as his device is unverified and not proven trustworthy.
5.4 No Client Vulnerabilities
Finally, we should mention that ZTNA isn’t an app that you install on your device. It offers no client, and as such, hackers can’t exploit any vulnerabilities on users’ devices. Not to mention that this makes it more suitable for BYOD devices that need to access the company’s resources quickly.
Instead of installing and setting up a VPN, which lasts long, the new device can access the information once it’s verified by ZTNA and the network administrator.
6. Conclusion: Which One Is Better?
To finish this ZTNA vs VPN duel, it’s clear that ZTNA is a better and more secure solution for enterprises. While a VPN will blindly trust any authorized device, ZTNA will scan and analyze various factors of each device, giving very limited access to the company’s assets due to its zero-trust approach.
With all users having the lowest possible level of privilege without authentication, the chances of compromising your corporate data are equal to zero. However, beware that VPNs and ZTNAs can be used together to form an end-to-end security system.
Users who work outside the company can get public Wi-Fi protection from a VPN, making sure that no malicious entities track their connections while doing the necessary work. ZTNA will make things more secure by preventing anyone unauthorized from accessing corporate information and files.
However, many companies go for either a VPN or ZTNA and that’s completely fine. If you don’t need that high level of security, VPNs will most likely do their job. But, if you work with more sensitive info and you have a large, productive, enterprise-level business, ZTNA is a more rational option.
We earn commissions using affiliate links.




![5 Best VPN Providers ([year]) [PC, iOS, Android] VPN](https://www.privateproxyguide.com/wp-content/uploads/2021/03/vpn-150x150.jpg)
![Best VPN for Kodi in [month] [year] Best VPNs for Kodi 2021 - To Avoid Buffering & Other Issues](https://www.privateproxyguide.com/wp-content/uploads/2018/05/kodi-launch-logo-150x150.jpg)
![CyberGhost VPN Review in [month] [year] cyberghost vpn](https://www.privateproxyguide.com/wp-content/uploads/2021/03/cyberghost-vpn-150x150.jpg)
![HideMyAss VPN Review in [month] [year] HideMyAss VPN Review 2021](https://www.privateproxyguide.com/wp-content/uploads/2018/06/hide-my-ass-review-homepage-150x150.jpg)
![How to Check if Your VPN is Working in [month] [year] How to Check if Your VPN is Working in 2021](https://www.privateproxyguide.com/wp-content/uploads/2018/07/How-to-Check-if-your-VPN-Connection-is-Secure-150x150.jpg)
![Best VPN for DraftKings in [month] [year] Best VPN for DraftKings](https://www.privateproxyguide.com/wp-content/uploads/2018/07/Best-VPN-for-DraftKings-150x150.jpg)
![Best Fortnite VPN in [month] [year] Best VPN for Fortnite](https://www.privateproxyguide.com/wp-content/uploads/2018/07/Best-VPN-for-Fortnite-BattleRoyale-150x150.jpg)
![5 Best VPN for Bet365 ([year]) [Fix not working] Best VPN for Bet365](https://www.privateproxyguide.com/wp-content/uploads/2018/08/best-vpn-for-bet365-150x150.jpg)
![Best Showbox VPN in [month] [year] Best VPN for Showbox](https://www.privateproxyguide.com/wp-content/uploads/2018/08/best-vpn-for-showbox-150x150.jpg)
![Best VPN for School WiFi in [month] [year] Best VPN for School WiFi in 2021 - How to Bypass VPN Bans](https://www.privateproxyguide.com/wp-content/uploads/2018/08/Best-VPN-for-School-College-150x150.jpg)
![Ivacy VPN Review in [month] [year] ivacy vpn](https://www.privateproxyguide.com/wp-content/uploads/2021/03/ivacy-vpn-150x150.jpg)
![Best Popcorn Time VPN in [month] [year] BEST VPN for Popcorn Time](https://www.privateproxyguide.com/wp-content/uploads/2019/01/best-vpn-for-popcorn-time-150x150.jpg)
![3 Best Apple TV 4K VPN in ([year]) & Setup Instructions Best VPN for Apple TV 4K 2021](https://www.privateproxyguide.com/wp-content/uploads/2019/02/Best-Vpn-for-apple-tv-4k-150x150.jpg)
![7 Best VPN for Hulu ([year]) [Fix not working] Best VPN for Hulu 2021](https://www.privateproxyguide.com/wp-content/uploads/2020/10/best-vpn-for-hulu-150x150.jpg)