AES-256 Encryption Explained Briefly:
AES-256-bit encryption turns plain text into cipher, making it completely unreadable. This is the highest encryption standard capable of securing information or data quickly. AES-256 encryption can’t be breached by brute force by a hacker or supercomputer because it would require millions of years.
In 2025, 256-bit AES encryption is a standard and is also known as bank-grade or military-grade given its wide use in the military, banking, VPN, cloud storage, and hundreds of other industries.
When you hear the word encryption, the first thing that comes to mind is a garbled mess of numbers and characters. This is often associated with encrypted data that can’t be read – for a reason. In simple words, encryption converts “ordinary” text into unreadable ciphertext.
Encryption is often associated with VPNs whose task is to encrypt your connection and make it unreadable by hackers, ISPs, and other entities. However, it’s more than a VPN-related feature. Encryption is used by governments and banks to secure confidential data.
This article will explain in depth what is encryption, how it works, and the meaning of AES-256 encryption, which is often deemed the higher standard. Here’s why AES-256 encryption is vital for keeping information private and unreadable.
What Is Encryption?
As explained in our introduction, we can look at encryption as a way of turning something readable into unreadable. Think of this sentence, which you can now read. But what if we moved each letter and put it randomly to create non-sensical words that you wouldn’t be able to understand?
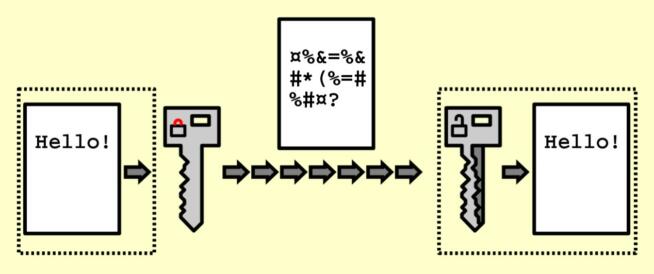
Courtesy of Wikipedia
The sentence would be “encrypted.” In the real world, things are far more complicated, as there are various encryption types. Before we explain them, we want to mention the encryption key, which is needed to encrypt AND decrypt information.
Earlier ROT ciphers were the pinnacle of encryption, especially the ROT13 cipher, which shifted each letter 13 places to add or remove encryption. However, as the ROT cipher is easy to brute-force and compromise, VPNs, governments, and other authorities turned to AES-256 encryption.
What Is AES-256 Encryption?
AES stands for Advanced Encryption Standard and it’s far better than now ancient ROT cipher. AES encryption is known as the block cipher. It splits data into blocks or chunks, that are then encrypted with different keys that differ in size. They range from:
- 128 bits
- 192 bits
- 256 bits
Simply put, 256-bit AES encryption results in 256 blocks of ciphertext from 256 blocks of “normal” text. This is the longest encryption key, which makes it incredibly tough to crack and compromise. To make it clear, even 128-bit encryption is nearly impossible to crack.
AES-256 encryption is identical – and even tougher, given its robustness. Experts often say that it would take millions if not billions of years for the fastest, most powerful supercomputer to brute-force this encryption. That’s why it’s often used by VPNs and governments to safeguard confidential info.
To explain AES-256-bit encryption better, it has 2256 combinations of letters and numbers that the hacker would need to break. If we do the math, that’s 1.1579209e+77 combinations – a number so long, it’s impossible to fit in one sentence without making it look silly.
Imagine having to brute-force through all of these just to decrypt a file or anything else. Even a NASA-scale supercomputer would crumble under pressure.
How Does AES-256 Encryption Work?
The base of every encryption is turning plain text or bits of data into a cipher by using an encryption key. This key is also used to later decrypt the text or data. As mentioned, AES encryption is called block cipher because it divides information into blocks, which is the first step of how AES-256 encryption works.
Usually, AES-256 encryption divides data into 4×4 columns, each 16 bytes in size. The next step is key expansion, which uses the first key and the AES algorithm to create several round keys. The initial round key is then added to data that’s been divided into smaller 4×4 columns.
In this process, each byte is replaced with another byte, after which, AES-256 encryption alters the rows of the 4×4 column. The second row moves to the left by one space, with the third row moving two spaces to the left and the process continues with all others.
After the “Shift” phase, the AES algorithm takes place and mixes all 4×4 columns and repeats the step of adding the round key, after which, the process continues according to the aforementioned principle. As you can see, AES-256 encryption is very complex.
What Makes AES-256 Encryption Unbreakable?
Because of its complexity, AES-256-bit encryption is unbreakable – at least by brute force. According to Progress, it would take 10-18 years to brute-force AES-256 encryption with a perfect mix of a powerful supercomputer and hacking talent.
One of the reasons is the use of the so-called symmetric keys. AES-256 encryption has a cryptographic key, which turns plain text into a cipher and vice versa, so the same key is used to decrypt files and information. That is simultaneously the definition of a symmetric encryption key.
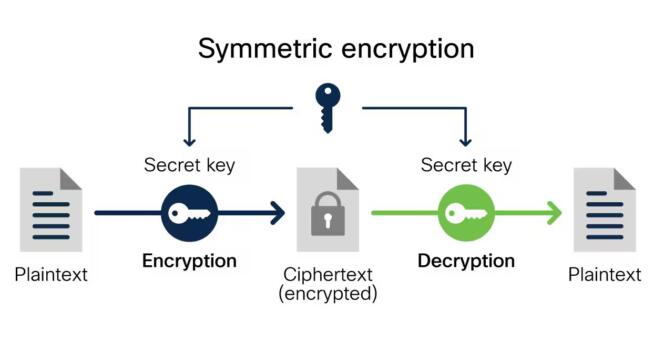
Courtesy of Cisco
Because of this, AES-256 encryption can encrypt and decrypt the bulk of data or files in a short period. Encryption speed is very fast and encryption requires fewer computing resources to run. In 2025, AES-256 encryption has become a gold standard, so to speak.
While its 128-bit and 192-bit counterparts are very capable, AES-256 encryption is on another level. When you think about it, there’s a reason why it’s called bank-grade or military-grade in many circles.
Conclusion
To conclude, 256-bit AES encryption is the safest, most secure level of encryption you can use. It’s impenetrable by brute force and would take billions of years to be broken even by the most skilled hackers. If you’re seeking a VPN with this encryption type, pretty much all use it.
The same applies to cloud storage providers whose bank-grade encryption keeps your files safe and sound. Being an industry-standard in 2025, you’ll see AES-256 encryption in many industries that aim to keep security vulnerabilities at bay and ensure safe and secure information and data exchange.
We earn commissions using affiliate links.


![Best Secure Email Providers for Privacy & Encryption [year] best private email providers](https://www.privateproxyguide.com/wp-content/uploads/2021/03/best-private-email-providers-150x150.jpg)
