Quick answer: The Best TOR Browser Alternative for Secure Browsing in 2025 is I2P!
Completely secure browsing is the biggest dream almost every user on the planet has. However, it is not easily attainable. There have been many programs that had the potential to provide us with the privacy we need, but not all of them were able to fulfill their promises. And, TOR is one of them.
Once highly regarded as the best program for secure browsing, TOR seems to have fallen from grace in recent years. So, the users of the deep web need answers to a few questions. What are the best alternatives to TOR? Why shouldn’t they use TOR in the first place? We did a bit of research on this subject, and we now have answers that will undoubtedly interest you. So, without further ado, let’s see how TOR browser works and the alternatives that you should start using instead of it.
NOTE: Stay safe while using TOR alternatives by adding an extra layer of protection with a VPN. See our list of recommended VPN-services.
1. Best TOR browser alternatives in 2025
As you can see, TOR is not a great solution anymore due to the attacks and its connection to the government. Thus, it’s vital to find other programs that will provide much-needed privacy and a worry-free experience. So, try these alternatives out and see if they work for you. Most users agree that they are viable options for avoiding TOR altogether, and we strongly suggest you consider them.
1.1 I2P
Website: geti2p.net
I2P, short for the Invisible Internet Project, is indeed a strong alternative to the Tor browser when it comes to secure and anonymous browsing. Here are some key reasons why I2P is a good choice for secure browsing:
-
Four Layers of Encryption: I2P employs a robust encryption system with four layers of encryption, which helps to ensure the utmost privacy and security. These multiple layers make it significantly difficult for anyone to intercept or trace your online communications.
-
End-to-End Encryption: I2P utilizes end-to-end encryption, meaning that your data is encrypted from the source (your device) to the destination (the recipient’s device). This ensures that only the intended recipient can decrypt and access the information, enhancing your online privacy.
-
Cryptographic Identifiers: I2P uses cryptographic identifiers as endpoints for communication. These identifiers are not linked to your actual identity or IP address, adding an extra layer of anonymity to your online activities.
-
Protection Against Third-Party Trackers: I2P is designed to protect users against third-party trackers, ensuring that your online behavior and activities remain private. This protection is crucial for preventing advertisers and data collectors from profiling your online habits.
-
Faster Performance: I2P is generally known for its faster performance compared to Tor. This speed advantage allows you to enjoy a smoother and more responsive browsing experience while maintaining your anonymity.
-
Optimized for Anonymity: I2P is specifically optimized for providing anonymity and privacy to its users. Its architecture and design are focused on achieving this goal, making it a reliable choice for those who prioritize anonymity and security.
-
Network Within a Network: I2P operates as a “network within a network,” creating a separate and isolated network layer on top of the regular internet. This isolation helps protect your online activities from surveillance and eavesdropping.
-
Diverse Use Cases: In addition to anonymous browsing, I2P supports various applications, including email, file sharing, and messaging. This versatility makes it a comprehensive solution for users who seek privacy across multiple online activities.
In summary, I2P offers a highly secure and anonymous browsing experience with multiple layers of encryption, end-to-end encryption, cryptographic identifiers, protection against trackers, faster performance, and optimization for anonymity. It is a solid alternative to the Tor browser for individuals who prioritize online privacy and security in the 21st century.
1.2 Yandex Browser
Website: browser.yandex.com
Yandex Browser is considered a good alternative to the Tor browser for secure browsing due to several key features and technologies it incorporates to enhance online privacy and security. Here’s why Yandex Browser is a reliable choice for those seeking anonymity and protection while browsing:
-
DNSCrypt Technology: Yandex Browser implements DNSCrypt technology, which plays a crucial role in enhancing online privacy. DNSCrypt encrypts the Domain Name System (DNS) traffic, preventing eavesdropping and unauthorized access to your DNS requests. This encryption helps hide your IP address and ensures that your online activities remain confidential.
-
Protection Against Fake Websites: Yandex Browser is equipped with mechanisms to protect users against phishing attacks and fake websites. It actively identifies and warns users about websites that attempt to impersonate legitimate sites to steal personal information, credit card details, usernames, and passwords. This feature helps users avoid falling victim to online scams and fraudulent websites.
-
Malware Protection: Yandex Browser goes beyond secure browsing by providing malware protection. It scans the internet for various types of malware, including viruses, trojans, and malicious scripts. This proactive scanning helps prevent users from inadvertently downloading or interacting with malicious content while browsing.
-
Privacy Features: Yandex Browser offers a range of privacy features and settings that allow users to customize their browsing experience. These features may include options to block third-party cookies, control tracking, and manage permissions for websites, providing users with greater control over their online privacy.
-
Secure Connection: Yandex Browser aims to establish secure connections whenever possible. It encourages websites to use HTTPS (Hypertext Transfer Protocol Secure) for encrypted data transmission, reducing the risk of data interception and man-in-the-middle attacks.
-
User-Friendly Interface: Yandex Browser provides a user-friendly interface that makes it accessible to a wide range of users. Its ease of use ensures that individuals, regardless of their technical expertise, can navigate the browser and its privacy features effectively.
-
Regular Updates: Like many modern browsers, Yandex Browser receives regular updates to address security vulnerabilities and improve overall security. Staying up-to-date with the latest version helps users benefit from the latest security enhancements.
In summary, Yandex Browser offers a secure and privacy-focused browsing experience through the use of DNSCrypt technology, protection against fake websites and malware, robust privacy features, secure connections, a user-friendly interface, and regular updates. These features make Yandex Browser a strong alternative to the Tor browser for users who prioritize online anonymity and security.
1.3 Epic Browser
Website: www.epicbrowser.com
Epic Browser is considered a good alternative to the Tor browser for secure browsing due to several features and capabilities that enhance privacy and security. Here are the reasons why Epic Browser is a reliable choice for those seeking a secure and private browsing experience:
-
User-Friendliness: Epic Browser is known for its user-friendly interface, making it accessible to a wide range of users, including those who may not be tech-savvy. Its straightforward design ensures that users can easily navigate and use the browser without encountering complex settings or configurations.
-
Fingerprinting Script Blocking: Epic Browser incorporates advanced privacy features, including the ability to block fingerprinting scripts. Fingerprinting is a technique used by websites and advertisers to track users across the internet by identifying unique browser and device characteristics. By blocking these scripts, Epic Browser helps users maintain anonymity and prevent tracking.
-
Privacy Protection: Epic Browser is designed to provide comprehensive privacy protection. It ensures that users can browse the internet without compromising their privacy, whether they want to hide their activities from their internet service provider (ISP) or use public networks securely. This focus on privacy safeguards user data and online activities.
-
Encrypted Proxy: Epic Browser offers an encrypted proxy feature that allows users to see the trackers that are following them while blocking them effectively. This transparency empowers users to understand and control the tracking elements on websites, contributing to a more private browsing experience.
-
Tracker Blocking: In addition to blocking fingerprinting scripts, Epic Browser provides built-in tracker blocking capabilities. It helps users avoid being tracked by online advertisers and third-party trackers, reducing the collection of personal data and enhancing online privacy.
-
Anonymous Browsing: Epic Browser supports anonymous browsing by routing traffic through a proxy server, obscuring the user’s actual IP address. This feature helps users maintain anonymity and makes it challenging for websites and trackers to trace their online activities back to their identity.
-
Protection on Public Networks: Epic Browser is suitable for use on public networks, where security risks are higher. It helps users protect their data and online activities from potential threats and eavesdropping when connecting to unsecured Wi-Fi networks.
-
Regular Updates: Like any secure browser, Epic Browser receives regular updates to address security vulnerabilities and improve overall security. Staying up-to-date with the latest version ensures users benefit from the latest security enhancements.
In summary, Epic Browser offers a user-friendly interface, fingerprinting script blocking, comprehensive privacy protection, encrypted proxy, tracker blocking, anonymous browsing, and protection on public networks. These features make Epic Browser a strong alternative to the Tor browser for users who prioritize online anonymity and security while maintaining ease of use.
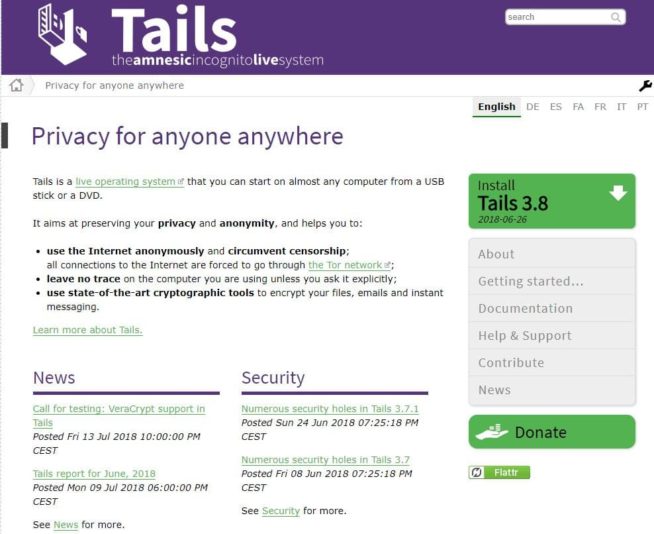
1.4 Tails
Website: tails.boum.org
Tails, short for “The Amnesic Incognito Live System,” is an excellent alternative to the Tor browser for secure browsing, emphasizing anonymity and privacy. Here are the key reasons why Tails is a strong choice for users seeking a secure and private online experience:
-
Ultimate Anonymity and Privacy: Tails is designed to provide the highest level of anonymity and privacy for users. It achieves this through a combination of encryption, secure communication tools, and a focus on leaving no traces behind. Your instant messages, emails, and personal files are all protected with strong encryption, ensuring that your data remains confidential.
-
Protection Against Censorship: Tails allows users to browse the web without the fear of being censored or monitored. It leverages the Tor network to route internet traffic through multiple volunteer-run servers, making it difficult for third parties to trace your online activities, access your location, or censor your access to specific websites or content.
-
Ease of Use: Tails is designed to be user-friendly and accessible to individuals with varying levels of technical expertise. Users can run Tails directly from a USB stick or a DVD, eliminating the need for complex installations or configurations. This ease of use ensures that users can start browsing securely without significant setup requirements.
-
Live Operating System: Tails operates as a live operating system, which means that it runs directly from external media (USB stick or DVD) without altering the host computer’s operating system. This approach provides isolation and ensures that no traces of your online activities are left on the host system.
-
Built-in Apps: Tails comes with built-in applications and tools that enhance your overall web browsing experience while maintaining privacy and security. These apps include secure email clients, instant messaging tools, and web browsers configured to work seamlessly with the Tor network.
-
Amnesic Nature: Tails is designed to be “amnesic,” meaning that it forgets everything about your activities once you shut it down. This ensures that no data or history is stored, further enhancing your privacy and security.
-
Open Source: Tails is open-source software, which means that its source code is publicly available and subject to review by the community. This transparency allows users to verify its security and trustworthiness.
-
Regular Updates: Tails receives regular updates to address security vulnerabilities and improve its overall security. Staying up-to-date with the latest version ensures users benefit from the latest security enhancements.
In summary, Tails is a live operating system that prioritizes ultimate anonymity and privacy, protection against censorship, ease of use, built-in apps, amnesic behavior, open-source nature, and regular updates. These features make Tails a robust alternative to the Tor browser for users who demand the highest level of security and privacy while browsing the internet.
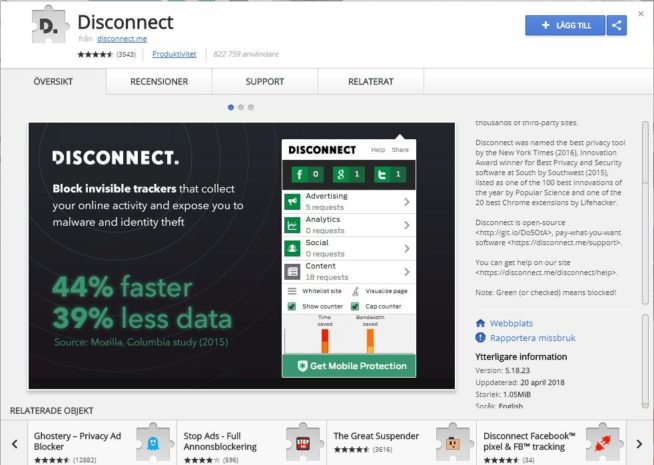
1.5 Disconnect
Website: chrome.google.com/webstore/detail/disconnect/
Disconnect is considered a good alternative to the Tor browser for secure browsing due to its focus on blocking tracking requests and enhancing online privacy. Here are the key reasons why Disconnect is a reliable choice for users seeking a secure and private online experience:
-
Tracking Request Blocking: Disconnect is primarily designed to block tracking requests made by websites and online services. These tracking requests are often used by companies like Facebook and Twitter to monitor users’ online activities and collect data for advertising and analytics purposes. By blocking these requests, Disconnect helps users maintain control over their online privacy and prevents third-party tracking.
-
Cross-Platform Compatibility: Disconnect offers compatibility with various operating systems, including iOS, Windows, and Android. Users can install Disconnect as a privacy extension or application on their devices, ensuring consistent privacy protection across multiple platforms.
-
Different Pricing Options: Disconnect provides users with flexibility in choosing from different pricing options and packages. While some features may be available for free, users can opt for premium plans to access additional privacy features and enhanced protection. These pricing options cater to a wide range of users with varying privacy needs and budget considerations.
-
Single Browser Use for Free: Users who prefer to use Disconnect on a single browser can do so for free. This option allows users to experience the benefits of tracking request blocking and enhanced privacy without any cost. It’s a convenient choice for those who want to explore Disconnect’s features before considering a premium plan.
-
Privacy Enhancement: Disconnect’s primary objective is to enhance online privacy by preventing tracking and blocking invasive third-party requests. This focus on privacy ensures that users can browse the internet without being constantly monitored, helping to protect their personal information and online activities.
-
User-Friendly Interface: Disconnect is designed to be user-friendly and accessible to a wide audience. Its intuitive interface allows users to enable or disable tracking protection easily, providing a hassle-free browsing experience.
-
Browser Extension: Disconnect typically operates as a browser extension, making it a lightweight and convenient privacy tool. Users can install the extension in their preferred web browser and activate it whenever they want to block tracking requests.
-
Enhanced Security: Disconnect’s tracking request blocking also contributes to enhanced security by reducing the exposure of user data to potential threats and unauthorized access.
In summary, Disconnect is a privacy extension and application that excels in blocking tracking requests from websites and online services. Its cross-platform compatibility, different pricing options, free single-browser use, privacy enhancement, user-friendly interface, and enhanced security make it a strong alternative to the Tor browser for users who prioritize online privacy and tracking prevention.
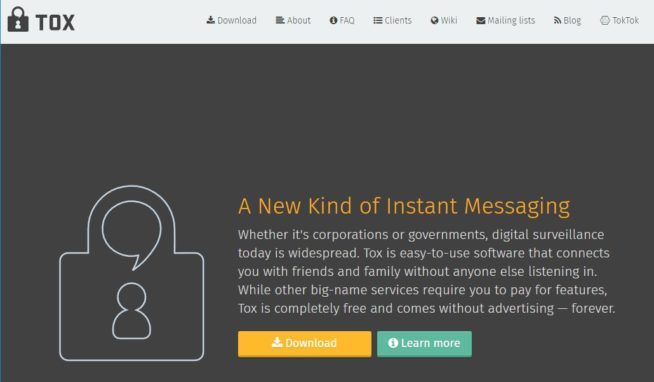
1.6 Tox
Website: tox.chat
Tox is included on this list because it is an excellent alternative to the Tor browser for secure instant messaging and private conversations. Here are the key reasons why Tox is considered a strong choice for users seeking secure and private communication:
-
End-to-End Encryption: Tox prioritizes security and privacy by implementing end-to-end encryption for all communications. This means that messages, voice calls, video calls, and other forms of communication are encrypted on the sender’s device and only decrypted on the recipient’s device. This encryption ensures that only the intended recipient can access and decipher the messages, making it extremely difficult for eavesdroppers or unauthorized parties to intercept or read the content.
-
Secure Instant Messaging: Tox provides a secure platform for instant messaging, allowing users to exchange text messages in real-time while ensuring that the content remains confidential. Users can chat with friends and contacts without worrying about their messages being intercepted or accessed by third parties.
-
Secure Video and Conference Calls: In addition to text messaging, Tox supports secure video calls and conference calls. Users can have face-to-face conversations or participate in group discussions with confidence, knowing that their communications are protected by strong encryption.
-
Peer-to-Peer Architecture: Tox operates on a peer-to-peer (P2P) architecture, meaning that communications are directly established between users without relying on central servers or intermediaries. This decentralized approach enhances privacy and reduces the risk of third-party surveillance or data retention.
-
User-Friendly Interface: Tox is designed to offer a user-friendly interface, making it accessible to a wide range of users. The application is typically straightforward to set up and use, allowing individuals to start secure communications without extensive technical knowledge.
-
Cross-Platform Compatibility: Tox is available on multiple platforms, including Windows, macOS, Linux, Android, and iOS. This cross-platform compatibility ensures that users can communicate securely across various devices and operating systems.
-
Community-Driven Development: Tox is an open-source project that benefits from community-driven development and contributions. This open nature allows the community to review the code, identify vulnerabilities, and enhance the security of the platform.
-
Privacy-Focused: Tox places a strong emphasis on user privacy, aiming to provide a secure and private communication platform. It does not require users to disclose personal information or use centralized servers, further safeguarding user data.
In summary, Tox is an excellent alternative to the Tor browser for secure instant messaging and private conversations. Its implementation of end-to-end encryption, support for secure video and conference calls, peer-to-peer architecture, user-friendly interface, cross-platform compatibility, community-driven development, and privacy-focused approach make it a robust choice for users who prioritize secure and private communication with friends and contacts.
1.7 FreeNet
Website: freenetproject.org
FreeNet is considered a strong alternative to the Tor browser for secure and anonymous browsing due to its unique features and decentralized, peer-to-peer architecture. Here are the key reasons why FreeNet is a good choice for users seeking secure online access:
-
Decentralized Peer-to-Peer Network: FreeNet operates on a decentralized peer-to-peer network structure. This means that users’ data and communications are distributed across multiple nodes (computers) within the network rather than relying on a central server. This decentralized approach enhances privacy and security, as there is no single point of failure or control.
-
Separate Protocols for User Interaction and Network Structure: FreeNet uses separate protocols for user interaction and network structure. This separation adds an extra layer of security, making it difficult for adversaries to track user data and online activities effectively.
-
DarkNet and OpenNet: FreeNet offers both DarkNet and OpenNet modes for user connections. In DarkNet, users connect with others they have exchanged public keys with beforehand. This high-security mode ensures that communications are encrypted and protected from eavesdroppers. In contrast, OpenNet allows users to connect securely without the use of public keys, providing flexibility in choosing their level of anonymity.
-
No Central Server: FreeNet does not rely on a central server, making it challenging for hackers or malicious actors to target a single point of entry or control. The absence of a central server enhances the network’s resilience to attacks and censorship attempts.
-
Data Encryption: Before storing data within the FreeNet network, all content is encrypted. This encryption ensures that stored data remains secure and inaccessible to unauthorized users, including potential hackers or attackers. Users can trust that their data is protected from exploitation.
-
High Level of Security: FreeNet is designed with a strong focus on security and privacy. It aims to provide users with a highly secure environment where they can access content, communicate, and share information without the risk of surveillance or unauthorized access.
-
Anonymity and Privacy: FreeNet prioritizes user anonymity and privacy. By distributing data across the network and implementing encryption, it ensures that users can browse and communicate anonymously, reducing the risk of tracking and monitoring.
-
Resistance to Censorship: FreeNet is designed to resist censorship and attempts to block access to information. Its decentralized nature and encryption measures make it challenging for authorities or third parties to restrict or monitor users’ online activities.
In summary, FreeNet is a secure and private alternative to the Tor browser, offering a decentralized peer-to-peer network, separate protocols for user interaction and network structure, DarkNet and OpenNet modes, absence of a central server, data encryption, high-level security, anonymity and privacy, and resistance to censorship. These features make FreeNet a robust choice for users seeking a secure and unhackable platform for online browsing and communication.
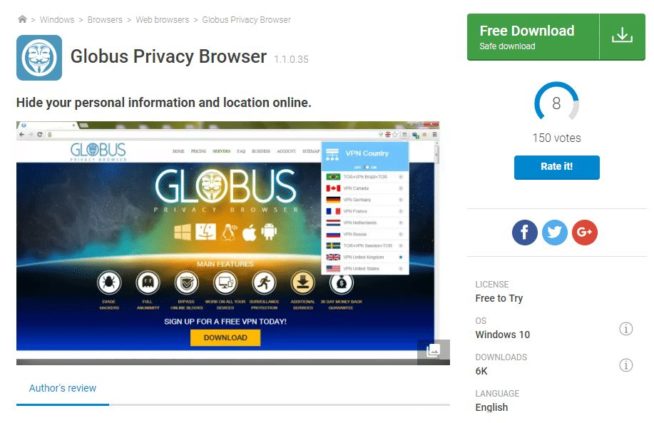
1.8 Globus
Website: download.cnet.com/Globus-Privacy-Browser/
Globus is considered a good alternative to the Tor browser for secure browsing due to its utilization of VPN servers and focus on providing users with enhanced online privacy and security. Here are the key reasons why Globus is a strong choice for users seeking secure and private web browsing:
-
VPN Servers for Total Privacy: Globus leverages VPN (Virtual Private Network) servers to offer users a high level of privacy while using the internet for personal use. VPNs create an encrypted tunnel between the user’s device and the server, ensuring that their online communication and activities remain hidden from prying eyes. This encryption enhances privacy by preventing eavesdropping and data interception.
-
Protection Against Third-Party Trackers: Globus includes features that prevent third-party trackers from collecting data about a user’s web activity. These trackers are often used by websites and advertisers to monitor user behavior and collect information for targeted advertising. By blocking these trackers, Globus helps users maintain their anonymity and prevent intrusive data collection.
-
Malware Protection: In addition to privacy features, Globus provides protection against malware and malicious software. This added layer of security safeguards users from potentially harmful content and online threats. It can help prevent malware infections and protect sensitive data from being compromised.
-
Availability Across Operating Systems: Globus is designed to be compatible with various operating systems, making it accessible to a wide range of users. Whether using Windows, macOS, or Linux, users can take advantage of Globus to enhance their online privacy and security regardless of their preferred platform.
-
User-Friendly Interface: Globus typically offers a user-friendly interface, making it relatively easy for individuals to set up and use. This ease of use ensures that users can enjoy enhanced privacy without the need for extensive technical knowledge or expertise.
-
Access to VPN Servers Worldwide: Globus often provides users with access to VPN servers located in different regions around the world. This global network of servers allows users to choose their preferred location and IP address, further enhancing anonymity and enabling access to region-restricted content.
-
Total Privacy with Minimal Effort: Globus aims to provide users with total privacy and security without requiring significant effort on their part. Once the VPN is activated, it automatically encrypts internet traffic and protects users from various online threats, allowing them to browse the web with confidence.
In summary, Globus is a solid alternative to the Tor browser for secure browsing. It achieves this through the use of VPN servers, protection against third-party trackers, malware defense, cross-platform compatibility, a user-friendly interface, access to global VPN servers, and a focus on providing total privacy with minimal user effort. Users can rely on Globus to enhance their online privacy and security while enjoying a seamless and protected browsing experience.
1.9 Ipredia OS
Website: www.ipredia.org
Ipredia OS is considered a good alternative to the Tor browser for secure browsing, particularly for Linux users, due to its focus on privacy and security. Here are the key reasons why Ipredia OS is a strong choice for individuals seeking a secure and private online experience:
-
Linux-Based Operating System: Ipredia OS is built on the Linux operating system, making it an excellent choice for Linux enthusiasts and users. Linux is known for its security features and open-source nature, which aligns with the principles of privacy and transparency.
-
Secure Browsing: Ipredia OS is designed to provide a secure browsing experience. It employs multiple layers of encryption to protect users’ online activities and ensure that their browsing paths remain invisible to potential threats such as hackers and trackers. This encryption helps maintain user privacy and data security.
-
Torrenting Support: In addition to secure browsing, Ipredia OS offers support for downloading torrents. Torrenting is a common method for sharing and downloading files, and Ipredia OS allows users to engage in torrent activities safely and anonymously. This feature is particularly useful for those who wish to download content while preserving their privacy.
-
Email Privacy: Ipredia OS extends its privacy features to email communication. Users can send and receive emails with the assurance that their messages remain confidential and can only be accessed by the intended recipients. This level of email privacy is essential for protecting sensitive information and maintaining communication security.
-
Multiple Layers of Encryption: Ipredia OS implements strong encryption techniques to secure users’ network traffic comprehensively. By employing multiple layers of encryption, it enhances the protection of data and ensures that users’ online activities are shielded from potential threats.
-
Access to the Deep Web: Ipredia OS provides users with access to the deep web, also known as the dark web. The deep web encompasses websites and content not indexed by traditional search engines. While it contains legitimate and valuable resources, it can also be a place where privacy is paramount. Ipredia OS enables users to explore this hidden part of the internet securely.
-
Stability and Reliability: Ipredia OS is known for its stability and reliability as an operating system. Users can trust it to provide a secure environment for their online activities, ensuring that their privacy remains intact while browsing, torrenting, or communicating.
In summary, Ipredia OS is a robust alternative to the Tor browser, particularly for Linux users. It offers a secure browsing experience, supports torrenting, ensures email privacy, employs multiple layers of encryption, grants access to the deep web, and provides a stable and reliable operating system for privacy-conscious individuals. Users can rely on Ipredia OS to protect their online privacy and security effectively.
1.10 Brave Browser
Website: brave.com
The Brave Browser is considered a good alternative to the Tor browser for secure browsing due to its focus on user privacy, speed, and protection against online tracking. Here are the key reasons why Brave Browser is a strong choice for individuals seeking a secure and privacy-centric online experience:
-
Privacy-Centric: Brave Browser places a strong emphasis on user privacy. It is designed to protect users from online tracking, data collection, and intrusive advertisements. It provides a secure and private browsing environment where users can navigate the web without the fear of their personal data being harvested.
-
Blocking Tracking: Brave Browser includes built-in features that block tracking cookies, scripts, and other mechanisms used by websites and advertisers to track user behavior. This ensures that users can browse anonymously and without being constantly monitored by third parties.
-
Identity Concealment: Brave Browser conceals users’ identities while they browse the internet. It prevents websites and online services from identifying or profiling users based on their online activities. This anonymity is essential for preserving privacy.
-
Ad Blocking: Brave Browser has a built-in ad-blocking feature that prevents intrusive and unwanted advertisements from displaying. This not only enhances the browsing experience by reducing distractions but also mitigates the risks associated with malicious ads.
-
No Access to Personally Identifiable Data: Brave Software, the company behind the Brave Browser, takes a privacy-first approach. They do not have access to users’ personally identifiable data or browsing history. This separation between user data and the browser’s developers ensures that sensitive information remains confidential.
-
Speed and Performance: Brave Browser is known for its speed and performance. It blocks resource-intensive ads and trackers, resulting in faster page loading times. Users can enjoy a smooth and efficient browsing experience without sacrificing privacy.
-
Rewards System: Brave Browser offers a unique rewards system called Brave Rewards. Users can opt to view privacy-respecting ads and receive Basic Attention Tokens (BAT) as rewards. These tokens can be used to support content creators and websites they appreciate, creating a fairer and more sustainable web ecosystem.
-
User-Friendly Interface: Brave Browser features a user-friendly interface that is easy to navigate. It offers a seamless transition for users familiar with other popular browsers, making it accessible to a wide range of individuals.
-
Cross-Platform Support: Brave Browser is available on multiple platforms, including Windows, macOS, Linux, Android, and iOS. This cross-platform compatibility allows users to maintain their privacy preferences across different devices.
In summary, the Brave Browser is a strong alternative to the Tor browser for secure and private browsing. It protects user privacy by blocking tracking, concealing identities, and offering an ad-free experience. With its focus on speed, user-friendliness, and a rewards system for content support, Brave Browser has gained popularity among privacy-conscious users seeking a secure online environment.
1.11 FreePto (discontinued)
Freepto is considered a good alternative to the Tor browser for secure browsing due to its focus on privacy, security, and ease of use. Here are the key reasons why Freepto is a strong choice for individuals seeking a secure and private online experience:
-
Privacy and Anonymity: Freepto is designed to provide strong privacy and anonymity for users. It is a favorite among activists and individuals who want to protect their online activities from government surveillance and tracking. By using Freepto, users can browse the internet without leaving traces of their online behavior.
-
Linux-Based Operating System: Freepto is a Linux-based operating system, which inherently provides a higher level of security compared to traditional operating systems. Linux is known for its robust security features, making it a suitable platform for privacy-focused users.
-
USB Stick Portability: One of the standout features of Freepto is its portability. Users can save the Freepto software onto a USB stick, allowing them to use it on any computer they have access to. This level of portability ensures that users can maintain their secure browsing environment regardless of the computer they are using, making it a convenient option.
-
Easy Installation: Freepto is designed to be user-friendly, and its installation process is straightforward. Users do not need advanced technical skills to set up and use the operating system. This accessibility makes it suitable for a wide range of individuals who prioritize privacy.
-
Pre-Built Apps: Freepto comes with pre-built applications that enhance the user’s online experience. These apps include an image editor, email client, and browser. Having essential tools readily available ensures that users can perform common tasks securely and privately.
-
Secure Communication: Freepto enables secure communication with peers, making it a valuable tool for activists and individuals who need to communicate confidentially. It employs encryption and privacy-enhancing technologies to protect sensitive communications.
-
Protection Against Government Surveillance: Freepto is favored by activists and privacy advocates for its ability to protect users against government tracking and surveillance. Its focus on anonymity and privacy ensures that users can browse the web without fear of being monitored by authorities.
-
Open Source: Freepto is open-source software, which means that its source code is publicly available for inspection and review. This transparency allows the community to verify its security and privacy features, increasing trust among users.
In summary, Freepto is a strong alternative to the Tor browser for secure browsing. It offers a Linux-based operating system that prioritizes privacy, anonymity, and security. Its USB stick portability, pre-built apps, and user-friendly design make it accessible to a wide range of users, including activists and individuals seeking protection against government surveillance and tracking.
1.12 Psiphon
Website: psiphon.ca
Psiphon is considered a good alternative to the Tor browser for secure browsing due to its ease of use, multi-platform support, and its ability to circumvent internet restrictions and protect users’ privacy. Here are the key reasons why Psiphon is a strong choice for individuals seeking secure and unrestricted access to the internet:
-
User-Friendly Interface: Psiphon offers a user-friendly interface that makes it accessible to a wide range of users, including those without technical expertise. Its simple design ensures that users can easily connect to the service and browse the internet securely.
-
Multi-Platform Support: Psiphon is available on multiple platforms, including Windows, Android, and iOS. This multi-platform support allows users to use Psiphon on their preferred devices, making it a versatile solution for secure browsing.
-
Circumvention of Internet Restrictions: Psiphon is specifically designed to circumvent internet censorship and restrictions. It uses a combination of VPN (Virtual Private Network) and SSH (Secure Shell) technologies to provide users with access to blocked or restricted content and websites, even in regions with strict censorship policies.
-
Protection from Internet Service Providers (ISPs): Psiphon helps protect users from monitoring and interference by internet service providers (ISPs). It encrypts the internet traffic, preventing ISPs from tracking users’ online activities or implementing bandwidth throttling.
-
Concealed IP Address: Psiphon conceals users’ IP addresses, adding an additional layer of privacy and anonymity. This feature prevents websites and online services from tracking users based on their IP addresses.
-
Anti-Censorship Features: Psiphon offers anti-censorship features that allow users to bypass online censorship and access content that may be blocked by governments or organizations. This feature is especially valuable for users in countries with strict censorship policies.
-
Pro Version: Psiphon offers a Pro version for users who require a higher level of privacy and advanced features. The Pro version may include faster connections, enhanced security, and additional server options.
-
Mobile Apps: Psiphon provides free mobile apps for both iPhone and Android users. These apps allow users to access Psiphon’s services on their smartphones or tablets, ensuring secure and unrestricted browsing on mobile devices.
In summary, Psiphon is a reliable alternative to the Tor browser for secure and unrestricted internet access. Its user-friendly interface, multi-platform support, circumvention capabilities, and privacy features make it a valuable tool for individuals seeking to bypass internet censorship, protect their privacy, and access blocked content. The availability of a Pro version and mobile apps further enhance its versatility and functionality.
2. What is TOR?
When it comes to the Internet, we tend to overlook our privacy in order to fulfill our basic browsing needs. However, some data is just not available for regular users who don’t know and cannot access the deep web. For that, you need an excellent privacy network or program; something that will allow you to securely browse, send, receive and share data you wouldn’t want anyone else to see. That is precisely why people use TOR. TOR is a US Navy-funded program that allows you to protect both your and your family’s privacy while browsing the Internet. What’s more, it lets you avoid censorship and gain access to websites that might be blocked in your country.
3. How does TOR work?
TOR uses virtual channels, also known as nodes, to bounce your path of Internet use in a randomized order. So, rather than using a direct connection, once you do something on the web, the path goes through those nodes in no particular order, thus protecting your privacy from others. Now, it sounds great, doesn’t it? It sounds like a dream come true for you if you want to protect your privacy without complicating things too much. No new routers, modems and other equipment – just one program and that’s it. But, if things were that straightforward, we wouldn’t be writing this article.
4. TOR issues
Even TOR has had a few slip-ups, which include the failure of its most basic trait: total privacy.
4.1 TOR & the Government
Just like we mentioned at the beginning of this article, TOR is funded by the US Navy. The reasoning behind it is that TOR allows the Navy to communicate without too much hassle and privacy concerns. However, some users view this as an issue. Anything that gets its funds from the government must somehow be under the control of that same government. After all, wouldn’t you want to control something that gives you power over many web users? Thus, a theory was born – the US Navy controls TOR and has a backdoor to it as well. Because of that, your data is never entirely private – at least not in the eyes of the US government.
This theory is somewhat far-fetched, but it’s one worth considering, especially if you are worried about your privacy. Furthermore, you ought to consider the fact that TOR does and probably will always attract the attention of law enforcement. Thus, even if you’re not doing anything wrong, you could easily find yourself on the other side of the law.
4.2 Hacking
Unfortunately, just like most programs, TOR can be hacked, and usually, it’s really not that hard to do that. Hence, by using it, you are risking far more than just your personal data. You are at risk of becoming the next target of hackers who may want to use that data against you.
4.3 Correlation attacks
Lastly, you ought to consider the fact that TOR is not immune to correlation attacks. They have happened before, and they can happen at any time. Even though the chances are not that high, the mere fact that a correlation attack can happen should make you shiver. After all, what’s the point of hiding your identity and protecting your privacy if you’re not secure 24/7?
With these correlation attacks, it’s possible to identify your IP address and the IP address of the user you’re talking to. For them to happen, the path would have to go through an entry and an exit relay that are under the control of the same entity. Additionally, there’s also a way of revealing your identity through traffic analysis. This technique allows for the router flow records to be analyzed if someone injects a modified TOR relay into the traffic. With it, around 81% of users can be identified, according to research conducted at Columbia University.
5. Final words
Just because TOR is not what it used to be, it doesn’t mean you should give up on your privacy protection. Any of these TOR alternatives will be an excellent choice for most users, and they will provide you with anonymity that will not cause headaches or worry any time soon.
We earn commissions using affiliate links.



![7 Best VPN for School WiFi [year]: Secure & Private Browsing Best VPN for School WiFi in 2021 - How to Bypass VPN Bans](https://www.privateproxyguide.com/wp-content/uploads/2018/08/Best-VPN-for-School-College-150x150.jpg)
![10 Best VPN for Chromebook [year]: Fast & Secure Browsing Best VPN for Chromebook](https://www.privateproxyguide.com/wp-content/uploads/2021/11/Best-VPN-for-Chromebook-150x150.jpg)
![Best Google Chrome VPN Extensions [year]: Fast & Secure Browsing Best VPN Extension for Google Chrome](https://www.privateproxyguide.com/wp-content/uploads/2021/12/Best-VPN-Extension-for-Chrome-1-150x150.jpg)

![Best VPN for Tor Browser [year]: Enhance Security and Privacy 5 BEST VPNs for Tor Browser 2021](https://www.privateproxyguide.com/wp-content/uploads/2019/11/Best-VPN-for-Tor-Browser-150x150.jpg)
![7 Best VPN for Microsoft Edge Browser [year]: Fast & Secure Best VPN for Microsoft Edge Browser](https://www.privateproxyguide.com/wp-content/uploads/2022/01/Best-VPN-for-Edge-Browser-150x150.jpg)
![Best Dropbox Alternatives [year]: Top Cloud Storage Solutions Best Dropbox Alternatives](https://www.privateproxyguide.com/wp-content/uploads/2021/11/Best-Dropbox-Alternatives-150x150.jpg)
![Best Zoom Alternatives [year] Top Picks for Online Meetings Best Zoom Alternatives](https://www.privateproxyguide.com/wp-content/uploads/2022/01/Best-Zoom-Alternatives-150x150.jpg)
![Best CCleaner Alternatives [year]: Top Tools for PC Optimization Best CCleaner Alternatives](https://www.privateproxyguide.com/wp-content/uploads/2022/10/Best-CCleaner-Alternatives-150x150.jpg)
![Best Free Word Processors [year]: Top Alternatives to Microsoft Word Best Free Word Processors](https://www.privateproxyguide.com/wp-content/uploads/2022/10/Best-Free-Word-Processors-150x150.jpg)
![Best Coinbase Alternatives [year] – Top Crypto Exchange Picks Best Coinbase Alternatives](https://www.privateproxyguide.com/wp-content/uploads/2022/12/Best-Coinbase-Alternatives-150x150.jpg)
![Best Omegle Alternatives [year]: Top Sites Like Omegle Best Omegle Alternatives](https://www.privateproxyguide.com/wp-content/uploads/2024/03/Best-Omegle-Alternatives-150x150.jpg)
Freenet isn’t secure either.
Canadian law enforcement runs modified code to trace people.
Brave uses google chrome to spy on you. Trash!
Exactly! Brave is PURE TRASH & anything that’s associated with Google.. People need to shut Google down honestly and stop giving them the power they don’t deserve .
Swordfish browser with the Ninja option is the best, only available in UnknownOS (Advanced Persistent Security). Never heard? Then, you must be a member of the ‘sheeple-movement’.