There is a range of special software to encrypt your hard drive or separate files on Windows 10. We are going to review the best of them and you will learn about their features and how to use them.
The best tools to encrypt your hard drive
1. BitLocker
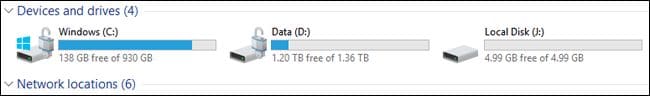
This is a standard disk encryption tool built into the Windows operating system. Many use it without installing third-party programs.
Indeed, why should they need to, if everything is already in the system? On the one hand, they are right. On the other hand, the code is closed, and there is no certainty that no backdoors were left in it for the FBI and other interested parties to be able to access the files.
Disk encryption is performed using the AES-128 or AES-256 algorithm. You are able to store the key in the Trusted Platform Module (TPM) on the computer itself or on a flash drive.
With TPM, the key can be obtained immediately after the system start. You can log in using a key on a flash drive or by entering a PIN code from the keyboard. You can use combinations of these methods that provide you with many options for restricting access: only TPM, TPM, and USB, TPM and PIN, or all three at once.
Pros
- You can control it through group policies.
- It encrypts volumes, not physical disks. This allows you to encrypt an array of several disks, which some other encryption tools cannot do.
- Supports the GUID Partition Table (GPT), which even VeraCrypt does not support. To encrypt a system GPT disk using VeraCrypt, you first have to convert it to the MBR format. In the case of BitLocker, this is not required.
Cons
- Proprietary closed code. If you keep the secrets of your household on your computer, BitLocker is great. However, if your disk is full of documents of national importance, it is better to find something else.
How to use BitLocker
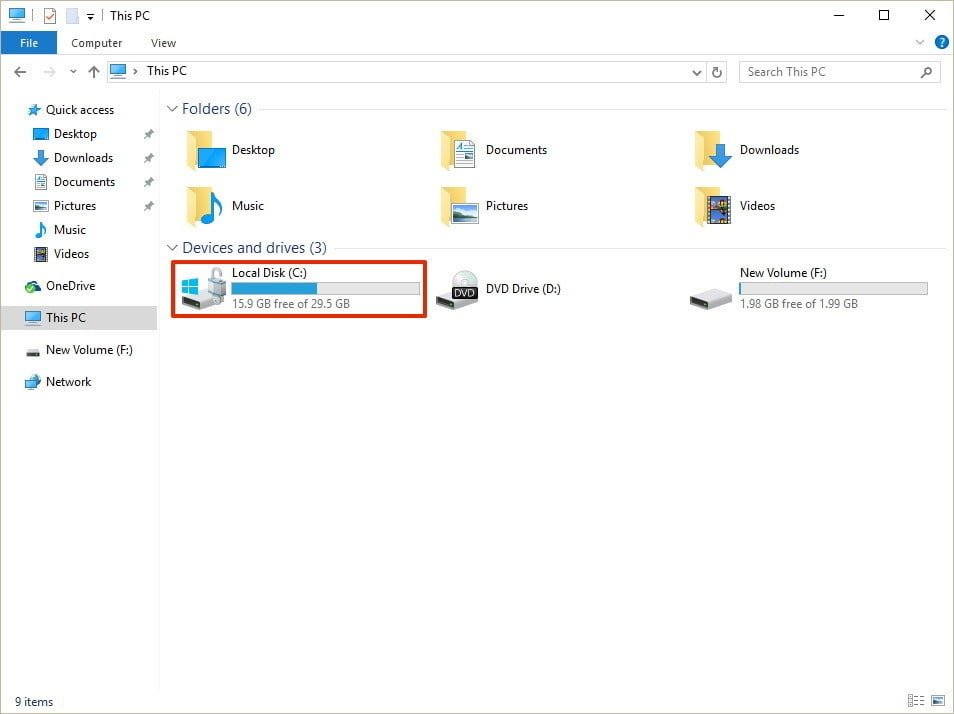
- In the search field on the taskbar, enter BitLocker and open it from the search results.
- Next to the drive you would like to encrypt, click on Turn on BitLocker.
- Select the way of unlocking the drive at the system startup. You can select Enter a password or Insert a USB flash drive. We will choose the password option.
- Create a password but keep in mind that it must be really strong and reliable. The tool describes what symbols you are able to use.
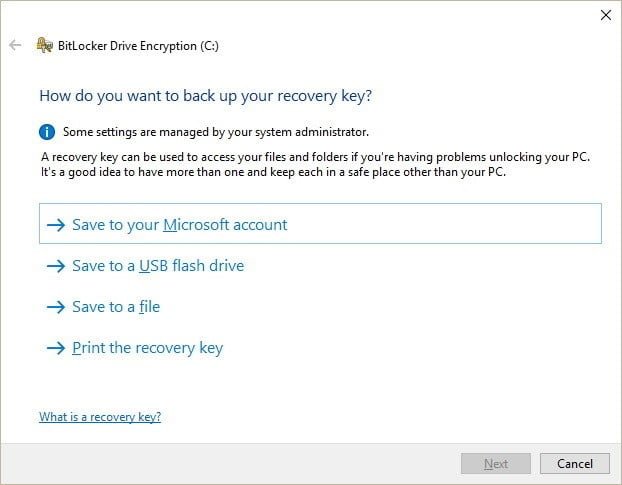
- Select the most suitable way to back up the recovery key:
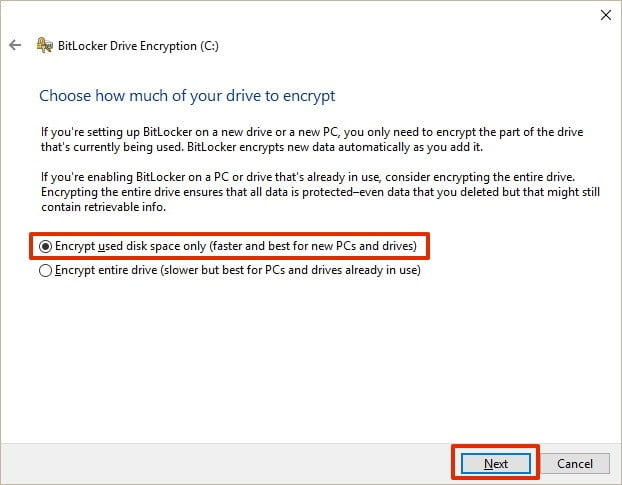
- Select whether you want to encrypt the entire disk or just a limited space.
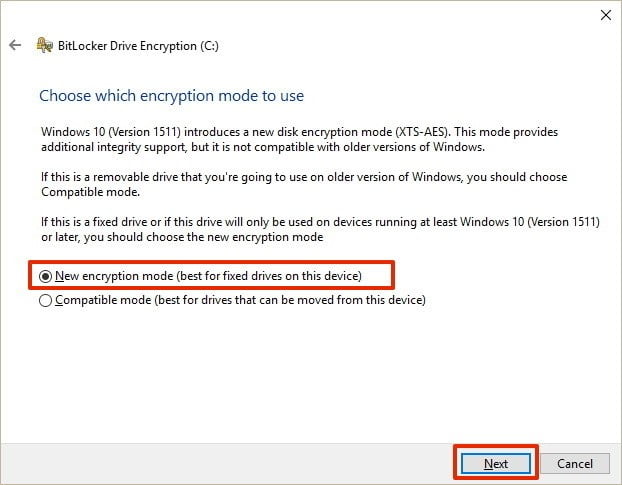
- Select the most suitable encryption mode:
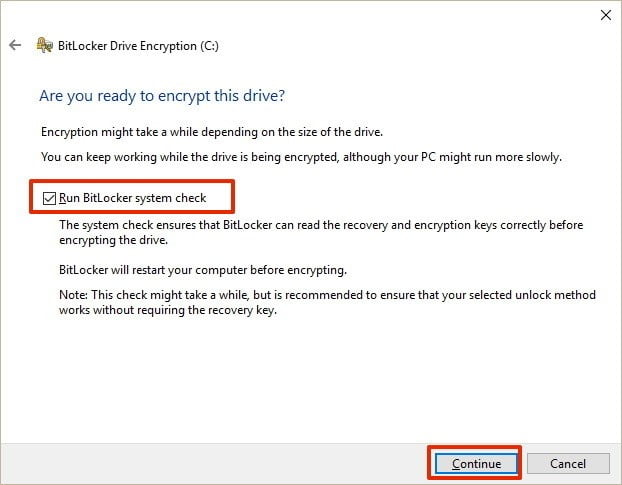
- Enable the Run BitLocker system check feature.
- Restart the computer to run the encryption.
- When the system restarts, type in the password you chose above.
- Wait until the system encrypts your drive. Once it is done, you will see the lock icon.
2. VeraCrypt
This is the most advanced clone of TrueCrypt which was the de facto international encryption standard. It has its own format, although it has the ability to work in TrueCrypt mode, which supports encrypted and virtual disks in the TrueCrypt format. You are able to use VeraCrypt with other encryptions tools.
TrueCrypt used 1000 iterations to generate the key to encrypt the system partition, while VeraCrypt uses 327,661 iterations. For standard (non-system) partitions, VeraCrypt uses 655 331 iterations for the RIPEMD-160 hash feature and 500,000 iterations for SHA-2 and Whirlpool features. This makes the encrypted partitions significantly more resistant to a brute-force attack, but also significantly reduces the performance of working with such a partition.
Pros
- Open source, as well as proprietary and more secure format of virtual and encrypted disks.
- Highly reliable protection with a strong encryption algorithm and hash features.
- Absolutely free to use without any limits.
Cons
- Lack of UEFI and GPT support.
How to use VeraCrypt
- Download and install the application like any other one. Just click on the installation file and follow the wizard instructions. For more convenient use, don’t forget to associate a .hc file extension with VeraCrypt.
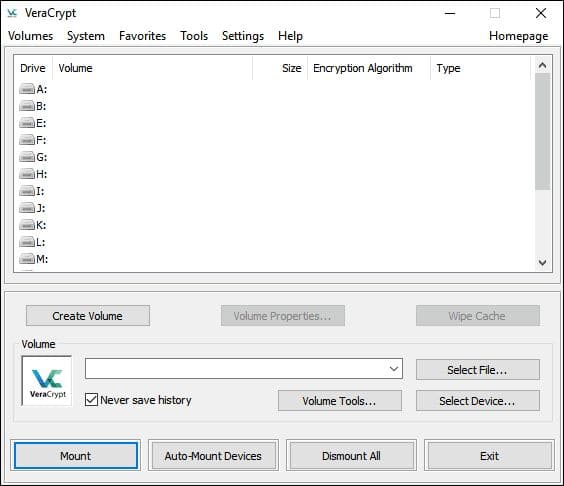
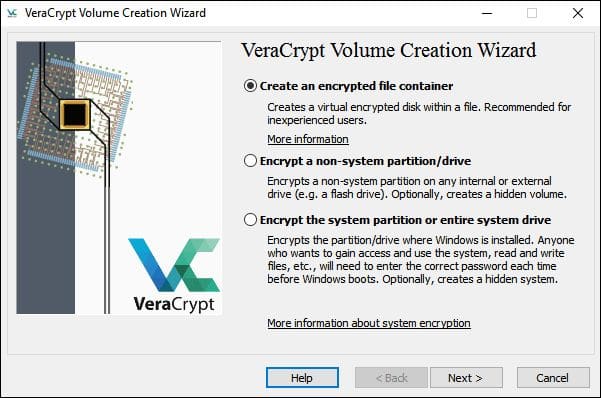
- Run the application, click on the Create Volume button, and select the type of volume you would like to create. Let’s choose the “Create an encrypted file container” option.
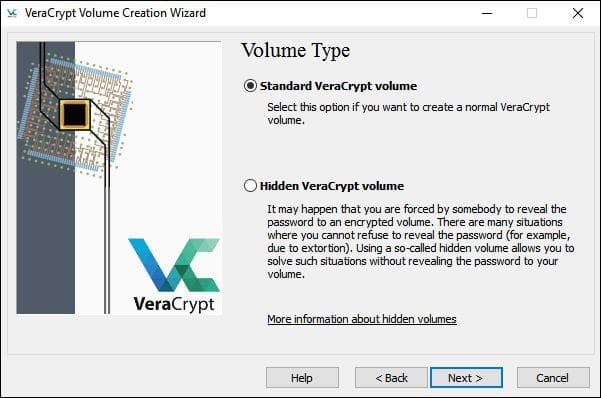
- Next, select Hidden or Standard volume. The Hidden volume option does not provide additional security but it will make the work more difficult. So, let’s select the Standard one.
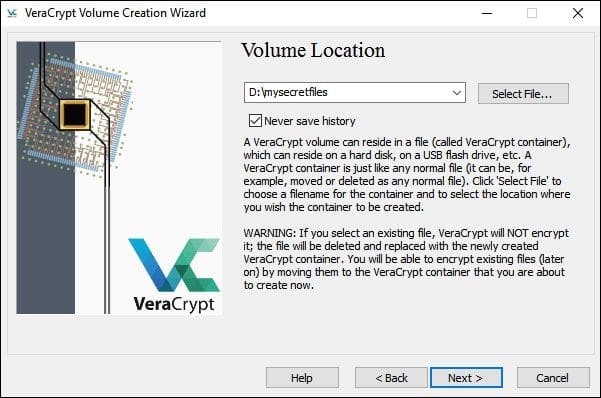
- Select the location where you are going to store the encrypted volume. Make sure the drive where you are going to store it has enough free space.
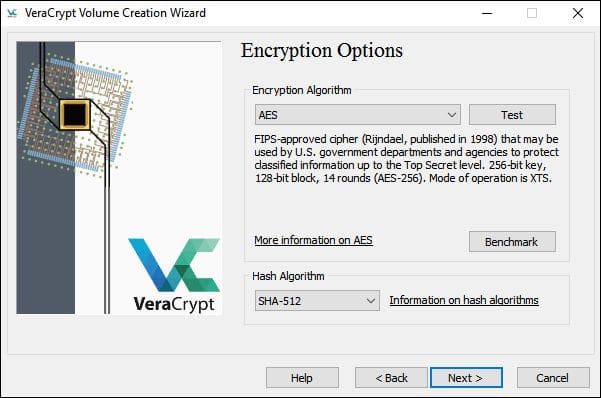
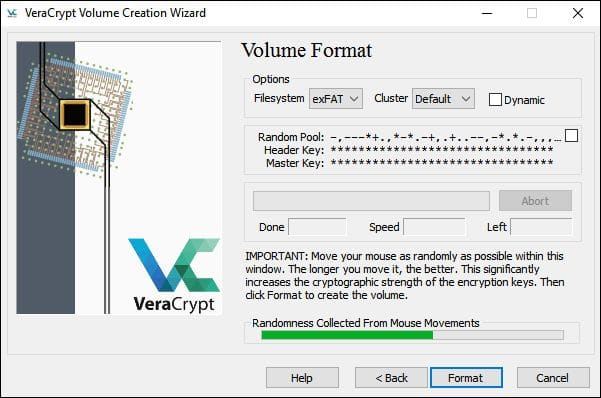
- Choose the encryption options. For example, let’s choose the AES and SHA-512. Be absolutely sure that they are extremely reliable. It will take at least a year to decrypt the volume encrypted using this combination.
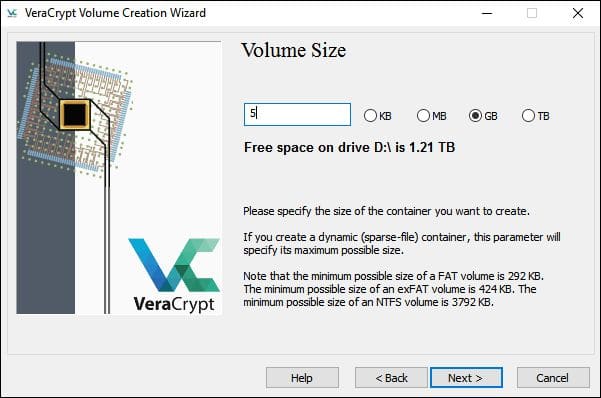
- Choose the volume size. Remember, it must not be bigger than the available free space. For example, let’s take 5 GB.
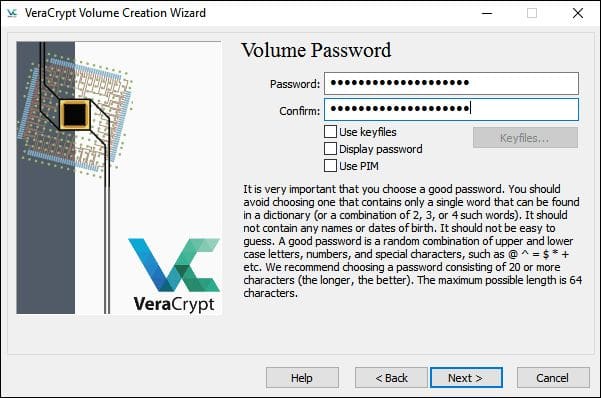
- Create a strong and reliable password. Make it at least 20 characters long.
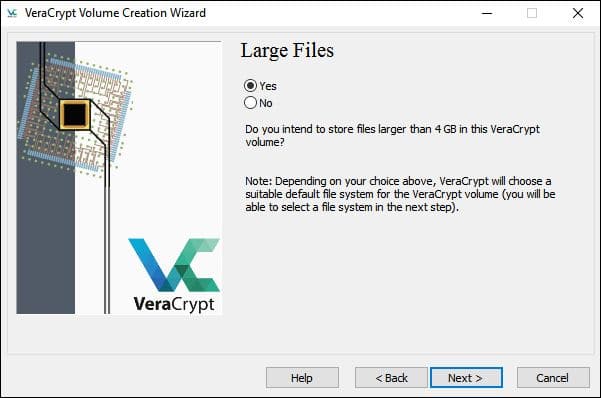
- Confirm whether you would like to store the large files. If you have files larger than 4 GB, select the Yes option.
- Move your mouse to generate random content for better security.
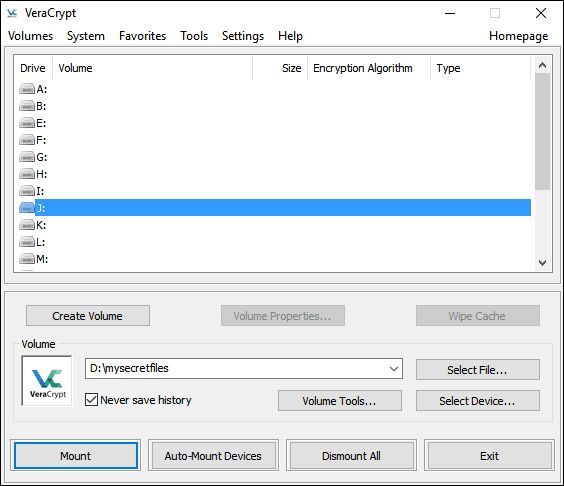
- The next important step is to mount the encrypted volume. Click on the Select File button and find the file in the folder you saved it. Give the volume a free letter.
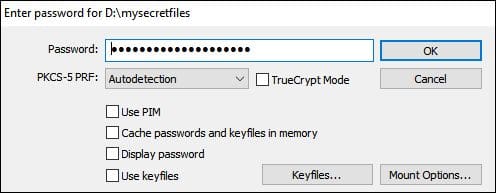
- Enter the password and click OK.
- In the File Explorer, you will see the new local disk with the letter you gave to the volume. This means you did everything correctly and the application created the encrypted drive successfully.
- Delete the original files you have just encrypted.
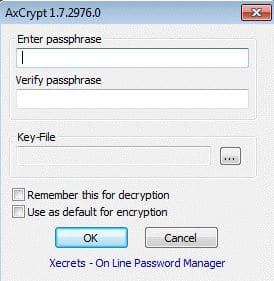
3. AxCrypt
AxCrypt is an open-source utility designed to protect user data using encryption. The program is distributed free of charge with somewhat limited functionality.
This software combines the encoder and encrypted file manager. The work is based on the AES-128 cryptographic algorithm (AES-256 is available in the Premium version).
All the user needs to do in order to protect his own documents is to register an AxCrypt account and specify the desired password. The file management process is carried out either by using the built-in manager or by using the corresponding items in the Windows context menu.
The utility supports work with popular cloud storages, first of all determining which ones are installed on the user’s computer, and then creating protected directories there. At the same time, there is absolutely no complication in the management of cloud services.
Pros
- Free product distribution.
- Open-source.
- Support for modern operating systems.
- Using the AES encryption algorithm as a basis.
- A clear interface that does not require difficult configuration.
- Quick and easy file management with a few mouse clicks.
- Ability to control from the context menu.
- Good community product support.
- Multi-language support and availability.
- Supports files larger than 4 GB.
Cons
- Despite the protection of the files using cryptographic methods, the attacker is able to simply delete them, gaining access to the PC, and thus cause harm to the user.
- The incompatible font used in the design of the program.
- The need to provide personal data, namely email addresses.
How to use AxCrypt
- Download and install the application.
- Select the folder you want to encrypt, click the right mouse button and select AxCrypt — Encryptin the context menu.
- Add the password and verify it. Make sure the password is at least 22 symbols long.
- The encrypted file will have the .axx extension.
- To open the file, enter the created password.
- If you do not want to encrypt the file anymore, click the right mouse button and select the Decrypt feature.
Encryption: general information
Encryption is the process of encoding information in a way it cannot be available to other people if they do not have the necessary key for decoding it. Encryption is usually used to protect sensitive documents, but it is also a good way to stop people from trying to steal your personal data.
The categories of encryption tools
In fact, there is a huge amount of software to encrypt the hard drive and separate files. Some of these programs use unique algorithms, other ones are quite similar. However, all of them can be nominally divided into 4 major categories.
- File and folder encryption utilities. These encryption tools work directly with files and folders, unlike utilities that encrypt and store files in volumes (archives, for example, in file containers). These encryption utilities can work in the “on demand” mode or in the “on-the-fly” mode.
- Virtual disk encryption utilities. Such tools work by means of creating volumes (encrypted containers or archives), which are represented in the file system as virtual disks having their own letter, for example, L. These disks can contain both files and folders. The computer file system can read, write, and create documents in real-time, for example, in open form. Such utilities work on-the-fly.
- Full-drive encryption utilities. These encrypt all the storage devices, for example, hard drives, partitions, and USB devices. Some of the utilities in this category can also encrypt the disk where the operating system is installed.
- Cloud encryption utilities. This represents a new category of encryption tools. These file encryption tools are used before downloading or syncing with a cloud service. Files are encrypted during transmission and during storage in the cloud. Cloud encryption tools use various forms of virtualization to provide access to the source code on the client-side. In this case, all the work happens in the on-the-fly mode.
Save the original files
After copying the files to a secure repository or after you have created their encrypted version, you definitely need to erase the unencrypted original ones.
Simply deleting them is not enough, even if you do it bypassing the recycle bin because the data remains on the disk, and data recovery programs can often bring it back.
Some encryption products are able to avoid this problem by encrypting a file, literally overwriting its encrypted version on a hard drive. This method is more common, although it is possible to offer safe deletion as an option. If you choose a product that does not provide this feature, you should find a tool to safely delete files.
The most reliable are the so-called shredders. However, you need to be extremely careful because after using this type of program, the chances of restoring the original are almost zero. Overwriting data before deleting is a fairly reliable anti-recovery thing. The magnetic data recordings on the hard drive are in fact not digital. In simple terms, this process involves zeroing out the data that remained after the deletion of the file.
If you really think that someone can use a specialized means to recover your sensitive files, you can install a safe removal utility. This type of program will overwrite the data several times so that even specialized recovery methods will not be able to recover your hard drive.
Encryption algorithms
The encryption algorithm is like a black box. You get back the dump of a document, image or another file that you upload to it. But what you see looks like nonsense.
You can turn this gibberish back into a normal document through a window using the same password that you entered during encryption. This is the only way to be able to see the original content.
Advanced Encryption Standard (AES) is the de facto international standard, and all the respective products support the AES encryption standard by default. At the same time, each software can use its unique solution. You will be able to decrypt the content only with the same software you used to encrypt it with. However, even those who support other algorithms, as a rule, recommend using AES. For a common user, AES is simply a great solution.
Public key cryptography and sharing
Passwords are important, and you should keep them private, right? Well, not when using public key infrastructure (PKI), which is used in cryptography. With PKI, you get two keys.
One of them is public and you can share it with anyone, register it in the exchange key, print it or tattoo it on your forehead — in general, do with it whatever you like. The other key is private and must be reliably protected.
If you want to send a secret document to someone, you just encrypt it with the public key. When you receive it, you can use it to decrypt the document.
It’s simple! Using this system the other way around, you can create a digital signature that confirms that your document came from you and has not been changed. How? Just encrypt it with your private key. The fact that your public key decrypts it is proof that you have the right to edit it.
PKI support is less common than traditional symmetric algorithms. If you want to share the file with someone and your encryption tool does not support PKI, there are other options for sharing. Many products allow the creation of self-decrypting executable files.
What to keep in mind
Operating systems are quite vulnerable: your personal data echoes — paging files, temporary files, power-saving mode files (sleep mode), deleted files, browser cache, etc. — will most likely, remain on any computer that you use to access data.
Highlighting this personal data eco is not a trivial task. If you need to protect the hard drive data while transferring or receiving them, then this is quite a challenge.
For example, when you create an encrypted archive of files or unzip such an archive, respectively, the original versions of the files or copies of the original files from this archive remain on the hard drive.
They can also remain in temporary storage locations (like Temp folders, etc.). And it turns out that the task of deleting these original versions becomes a task of not simply deleting these files by means of the “delete” command.
The fact that the encryption program works does not mean that it is secure. New encryption utilities often appear after someone reads application cryptography, chooses an algorithm, and starts developing. Someone may even use a proven open-source code, implement a user interface, makes sure it works and thinks that this is all over. But it is not. Such a program is probably filled with fatal bugs. “Functionality does not equal quality, and no amount of beta testing will ever reveal a security flaw. Too many products are merely buzzword compliant; they use secure cryptography, but they are not secure,” said Bruce Schneier from Security Pitfalls in Cryptography.
Using encryption is not sufficient to ensure your data security. There are many ways to bypass the protection, so if your data is very secret, then you must also think about other ways to protect it.
Conclusion
In this review, we mentioned three of the best apps available at the moment to encrypt your hard drive. In reality, there are many more of them. Which tool do you prefer?
We earn commissions using affiliate links.






![Best SSD External Hard Drives [year] – Fast and Reliable Storage Best SSD External Hard Drives](https://www.privateproxyguide.com/wp-content/uploads/2022/08/Best-SSD-External-Hard-Drives-150x150.jpg)
![Best PS5 External Hard Drives [year]: Expand Your Storage Best External Hard Drive for PS5](https://www.privateproxyguide.com/wp-content/uploads/2022/08/Best-External-Hard-Drive-for-PS5-150x150.jpg)
![Google Drive Review: Features, Pros & Cons Explained [year] google drive](https://www.privateproxyguide.com/wp-content/uploads/2021/03/google-drive-150x150.jpg)
![pCloud vs Dropbox vs Google Drive vs Onedrive vs Mega [year] pCloud vs Dropbox vs Google Drive vs Onedrive vs Mega 2021](https://www.privateproxyguide.com/wp-content/uploads/2020/04/pCloud-vs-Dropbox-vs-Google-Drive-vs-Onedrive-vs-Mega-150x150.jpg)


![Best Password Managers for Windows, iOS & Android [year] best password managers 2021](https://www.privateproxyguide.com/wp-content/uploads/2021/03/best-password-managers-2021-150x150.jpg)

![Best Android Emulators for PC and Windows 10 in [year] Best Android Emulators for PC](https://www.privateproxyguide.com/wp-content/uploads/2019/10/10-best-android-emulators-for-pc-150x150.jpg)
![Best Cloud Hosting Providers for Linux & Windows [year] best cloud hosting providers](https://www.privateproxyguide.com/wp-content/uploads/2021/03/best-cloud-hosting-providers-150x150.jpg)