IKEv2/IPSec Quickly Explained:
In short, IKEv2/IPSec is a highly secure VPN protocol with excellent performance and fast speed. It uses AES-256 encryption, offers stable connections, and works well on mobile devices. IKEv2 is faster than OpenVPN but is slightly less popular because of its closed-source nature, incompatibility with some devices, and likeliness to be blocked by firewalls and network administrators.
As a whole, it’s among the safest VPN protocols with support for MOBIKE, NAT-T, and Asymmetric Authentication, which makes it superior to IKEv1 – an initial iteration of IKE.
IKE, also known as “Internet Key Exchange” is a popular VPN protocol known for a blend of performance and security. However, if you’re an average VPN user, you might be wondering why is the protocol so popular and is often used as a substitute for OpenVPN.
In today’s guide, we’ll explain what is the popular IKEv2 protocol, as well as its v1 and v3 iterations. Also, we’ll explain why it’s frequently combined with IPSec to further secure your connection and ensure better connection stability and reliability.
What Are VPN Protocols?
VPNs rely on a myriad of security protocols to connect your device to the VPN server. This is the main function of a VPN protocol, in fact. VPN protocols generate the encryption keys after authenticating the VPN server and the user’s device. This key can then be used by both.
Modern VPNs rely on various protocols, such as OpenVPN, WireGuard, NordLynx, Lightway, and IKEv2/IPSec. The latter is especially interesting, as its ease of implementation allows it to be used on mobile devices. In particular, IKEv2 is very popular on iOS devices because of its native incompatibility with OpenVPN. But what is IKEv2/IPSec?
IKEv2/IPSec: What Is It? How Does It Work?
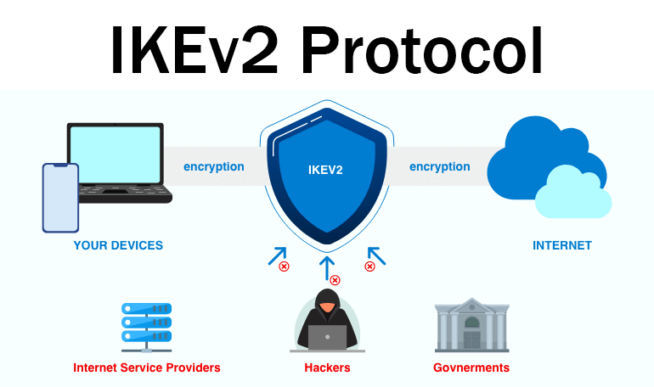
As said, IKE stands for “Internet Key Exchange” and the “v2” part stands for the second version – it was developed by Microsoft and Cisco. IKEv2 is based on IPSec, which now stands for “Internet Protocol Security.” Think of IPSec as an authenticator that ensures secure traffic.
IPSec is crucial for connecting devices and adding encryption, which allows for safe data travel. While IPSec and IKEv2 can be used separately (very rare), they’re almost always combined to get the best effect. IKEv2 is fast and stable, allowing for a smooth and reliable connection.
Courtesy of ARAVIND .S (LinkedIn)
On the flip side, IPSec provides excellent security, preventing third-party tracking and monitoring. In 99% of the cases, when you see the IKEv2 VPN protocol, it’s combined with IPSec. Now, we need to see how IKEv2 works. As expected, its basic function isn’t different from any other VPN protocol.
The primary function is to connect the server and the VPN client. IPSec is here to authenticate both sides with a private key, setting up so-called exchange rules. In this process, the encryption method is determined, after which, the connection is established.
Apart from IPSec, IKEv2 also handles some of the security attributes (Security Association or SA). For example, the VPN server and VPN client need the same configurations for successful data exchange and IKEv2 provides both with an identical (symmetric) encryption key for this to happen.
However, while IPSec sets all of the aforementioned rules and assigns a private key before establishing a connection, IKEv2’s key is used when the data has already passed through the VPN tunnel, at the end.
IKEv1 vs IKEv2 vs IKEv3 Differences
Regardless of the number that sits at the end of each IKE protocol, it’s vital to know it works the same way. Naturally, this begs the question of how are they different and why is IKEv2 the most popular option. For the start, IKEv1 is an old protocol introduced in 1998.
IKEv2 was released in 2005 and is, simply put, a better version. IKEv2 is known for EAP or Extensible Authentication Protocols support, which allows for remote access. Also, being an improvement over IKEv1, IKEv2 tends to consume less bandwidth and is much faster.
Let’s not forget that IKEv2 supports NAT-T (Network Address Translation-Traversal), which allows for superior, more stable performance. MOBIKE (Mobility and Multi-homing Protocol) is another thing that IKEv1 doesn’t support but is in IKEv2 and enhances the performance and overall security.
On the security side, IKEv2 is also quite better. For example, IKEv2 uses separate encryption keys for each side (VPN client and the VPN server) and supports many complex encryption algorithms compared to IKEv1. Some of them include ChaCha20, Camellia, AES, and others.
IKEv3 is frequently mentioned online but this protocol is more a theory than practice. IKEv2 is the most modern iteration at the time of writing, with IKEv3 being only viable on paper. VPNs like NordVPN, CyberGhost, and others still use IKEv2 as the best version of the IKE protocol.
In the future, we might see IKEv3 come to fruition but in 2024, that’s still not the case.
IKEv2 vs IPSec vs OpenVPN: Which Protocol Is the Best?
There’s no point in comparing IPSec to IKEv2, as they’re so different. This is why they go well together. IPSec is extremely secure, while IKEv2’s strength is connection speed. You’ll rarely – if ever – see IPSec being used by VPNs as separate protocols.
In 99.99% of the cases, it’s packed with IKEv2 under the name of IKEv2/IPSec or simply IKEv2. This “hybrid” allows you to enjoy short connection times, faster VPN speeds, and impeccable security. Now, if we compare IKEv2/IPSec and OpenVPN, which protocol is superior?
According to cybersecurity experts like, for example, Avast, IKEv2 has a slight edge over OpenVPN in overall performance, speed, and stability. OpenVPN is, however, more secure, as it’s open-source, supports additional customization, and isn’t blocked by firewalls and IT administrators.
OpenVPN can also help to bypass censorship in some countries when it’s paired with obfuscation. It’s no wonder NordVPN’s obfuscated servers rely on OpenVPN TCP and work well in China.
IKEv2 Downsides
IKEv2/IPSec sounds almost perfect on paper but it has a few drawbacks worth considering.
- It’s not open-source. IKE was developed by Microsoft and Cisco and the protocol is closed-source. This is a major drawback because it leaves no room for improvement. Open-source protocols like OpenVPN and WireGuard allow everyone to inspect them, which permits cybersecurity experts to audit these protocols and apply security improvements.
- Device compatibility. IKEv2/IPSec works on Windows, iOS, and macOS pretty well. Sadly, that’s where device compatibility ends, as all other devices usually rely on either OpenVPN or WireGuard, with the IKEv2 setup being far more complicated – if at all possible.
- It requires specific ports. 443 and 80 are typical ports used for VPN and HTTP connections. 443 is used for OpenVPN, while port 80 is used for HTTP connections. IKEv2 uses port 500 (UDP), which can often be closed by IT administrators or firewalls because of safety concerns.
The Bottom Line
With a huge selection of VPN protocols, IKEv2 is still among the best options, despite the launch of WireGuard. IKEv2 is highly secure, it’s stable and performs well. Its security is very strong, with AES-256 encryption support and IPSec authentication for added safety.
Indeed, IKEv2 won’t work on every device, it’s closed-source, and requires Port 500 UDP to work. However, if you have a modern macOS/Windows PC or an iPhone, IKEv2 will likely work well. Most mobile VPNs use IKEv2 by default on iOS/macOS without the need for manual setup.
We earn commissions using affiliate links.









![50 Best Instagram Bots [year] (for Followers That Still Work) best instagram bots 2024](https://www.privateproxyguide.com/wp-content/uploads/2021/03/best-instagram-bots-2021-3-150x150.jpg)

![Is Mobdro Legal and Safe to Use in in [month] [year]? Is Mobdro Legal and Safe to Use](https://www.privateproxyguide.com/wp-content/uploads/2020/10/Is-Mobdro-Legal-and-Safe-to-Use-150x150.jpg)

![Lost Ark VPN Alternatives ([year]) Unblock Korea and Russia Best VPN for Lost Ark](https://www.privateproxyguide.com/wp-content/uploads/2022/04/Best-VPN-for-Lost-Ark-150x150.jpg)

![Best Wall Mount Server Racks and Cabinet Enclosures in [year] Best Wall Mount Server Racks and Cabinet Enclosures](https://www.privateproxyguide.com/wp-content/uploads/2022/07/Best-Wall-Mount-Server-Racks-and-Cabinet-Enclosures-150x150.jpg)
![School and College VPN Alternatives ([year]) Best VPN for School and College-4](https://www.privateproxyguide.com/wp-content/uploads/2022/09/Best-VPN-for-School-and-College-4-150x150.jpg)